Predicting Demand for Specialized Cybersecurity Roles: Ethical Hacking & Threat Intelligence (2026–2030)
Cybersecurity hiring through 2030 will not reward “generalists who can do a bit of everything.” It will reward specialists who can break systems legally and specialists who can turn messy signals into decisions. Ethical hacking is becoming the validation layer for every control you claim works. Threat intelligence is becoming the prioritization layer for every alert you cannot afford to chase. The demand spike is already visible in how SOCs are evolving, how ransomware crews operate, and how executive teams fund measurable outcomes instead of vague security promises.
1) Why Ethical Hacking and Threat Intelligence Become “Core” Roles by 2030
The biggest driver is attacker efficiency. Modern adversaries do not need exotic malware when they can use misconfigurations, credential reuse, and weak identity workflows to pivot fast. That is why practical offensive skill sets keep rising, especially when paired with real-world response thinking from an incident response plan and detection alignment through a mature SIEM.
Ethical hacking demand grows because leadership is tired of faith-based security. Boards want proof that segmentation holds, controls stop lateral movement, and privileged access is not a single point of failure. Those “proofs” come from repeatable testing, guided by frameworks SOC leaders already use when building careers from SOC analyst to SOC manager and when aligning security outcomes at the CISO level.
Threat intelligence demand grows because alert volume keeps climbing, but security budgets and headcount do not scale the same way. A threat-intel function becomes the filter that decides what to prioritize, what to automate, and what to ignore. When intel is done correctly, it improves hunting, detection logic, and containment decisions that flow into the same IRP execution model your team must follow under pressure.
A second driver is ransomware economics. Attackers monetize speed, disruption, and credibility. Defenders must reduce dwell time and block common intrusion paths. That pushes demand for both ethical hackers who can simulate real intrusion patterns similar to those discussed in ransomware response and recovery and threat-intel specialists who can map active campaigns, initial access trends, and known TTPs from analyses like ACSMI’s state of ransomware coverage.
A third driver is cloud and SaaS sprawl. Traditional perimeter thinking fails. Your defenders need specialists who understand how identity, API usage, and endpoint behavior connect, which is why intel teams increasingly partner with SIEM engineering and endpoint telemetry programs described in ACSMI’s endpoint security research. And when this becomes leadership-facing, it ties into program maturity expectations discussed in the security manager to director roadmap.
| Role | What They Deliver | Why Demand Is Rising | Key Skills | Best Fit Environments |
|---|---|---|---|---|
| Ethical Hacker (General) | End-to-end attack simulation | Execs want proof of control effectiveness | Recon, exploitation, reporting | Mid-enterprise |
| Web App Penetration Tester | Finds auth, logic, API flaws | APIs drive revenue, APIs get abused | OWASP, auth bypass, testing | SaaS |
| Cloud Penetration Tester | Validates cloud misconfig & identity abuse | Cloud sprawl expands attack paths | IAM abuse, cloud tooling | Hybrid orgs |
| Red Team Operator | Stealth intrusion exercises | Boards ask “can you stop a real attacker?” | C2, evasion, persistence | Large enterprise |
| Purple Team Engineer | Maps attacks to detections & fixes gaps | ROI-driven security engineering | ATT&CK mapping, tuning | Mature SOC |
| Exploit Validation Specialist | Confirms real exploitability | Patch fatigue needs smarter prioritization | PoC analysis, risk ranking | Regulated |
| Attack Surface Analyst | Finds exposures before attackers do | External exposure changes daily | Asset discovery, OSINT | Any |
| Social Engineering Specialist | Tests people + process failures | Phishing still drives initial access | Pretexting, awareness metrics | Remote-first |
| Threat Intelligence Analyst | Prioritizes threats and enriches detections | Teams cannot chase every alert | TTPs, IOC hygiene, reporting | SOC |
| CTI Collection Lead | Builds reliable intel sources | Bad intel wastes time and money | Source evaluation, workflows | Enterprise |
| Threat Hunter | Finds stealthy intrusions with hypotheses | Attackers aim for low-noise persistence | Hunting, queries, triage | Mature telemetry |
| Detection Engineer | Builds high-fidelity detections | Fewer alerts, better alerts | SIEM logic, tuning, testing | SOC |
| Malware Triage Analyst | Analyzes suspicious files quickly | Faster containment decisions | Static/dynamic analysis | IR teams |
| Ransomware Intelligence Specialist | Tracks crews, TTP shifts, extortion patterns | Ransomware remains business-critical risk | Campaign tracking, playbooks | Any |
| Threat Modeling Engineer | Anticipates abuse paths in systems | Secure-by-design pressure increases | Modeling, controls mapping | Product orgs |
| OSINT Investigator | Finds external exposure & actor context | Brand, exec, vendor risk expands | OSINT tradecraft | Any |
| Dark Web Monitoring Analyst | Finds leaked creds/data signals | Credential leaks drive account takeover | Leak validation, response triggers | SaaS |
| Insider Risk Analyst | Detects misuse and policy violations | Data theft is often quiet | Behavior analytics, investigations | IP-heavy |
| Third-Party Risk Intelligence | Assesses vendors with intel signals | Supply chain incidents keep happening | Risk scoring, monitoring | Vendor-heavy |
| API Abuse Specialist | Detects automation and bot-driven fraud | APIs are high-value targets | Abuse patterns, rate limiting | SaaS |
| Security Automation Engineer | Automates enrichment and response | Headcount constraints push automation | SOAR logic, scripting | Lean SOC |
| Deception Engineer | Deploys honey tokens/files to catch intrusions | Stops low-noise attackers earlier | Trap design, monitoring | High-value |
| Incident Intelligence Coordinator | Keeps intel aligned to active incidents | Better decisions during crises | Comms, triage, tracking | IR teams |
| Threat Intel Product Manager | Turns intel into usable internal services | Intel must be operational, not reports | Stakeholders, metrics | Large orgs |
| Security Researcher | Finds novel weaknesses and tactics | Attack tech keeps evolving | Research, reverse engineering | Labs |
| Digital Forensics Analyst | Preserves evidence and rebuilds timelines | Regulators and litigation demand rigor | Forensics, chain of custody | Regulated |
| Security Metrics Analyst | Measures control effectiveness & risk movement | Leadership wants outcomes, not noise | KPIs, reporting | Any |
| Compliance Intelligence Analyst | Tracks regulatory shifts and maps to controls | Compliance pressure keeps increasing | Regulatory mapping | Regulated |
| Security Program Leader (Specialized) | Builds roadmap and funding narrative | Cyber becomes board-level risk | Strategy, prioritization | Enterprise |
2) Demand Forecast 2026–2030: What Hiring Managers Will Actually Pay For
Ethical hacking demand shifts from “annual pentest” to continuous validation
Organizations will still do compliance-driven testing, but the real growth comes from operational validation. Hiring managers are increasingly funding roles that can test controls continuously, map results to detection, and prove reduced risk. That is the same mindset shift you see when teams mature from a basic SOC into a high-performing operation guided by SIEM discipline and standardized response through an IRP.
This demand is strongest in environments where downtime is unacceptable and ransomware is existential. Ethical hackers who can emulate intrusion patterns that lead to ransomware outcomes become high leverage, especially when they can connect their findings to practical improvements aligned with ransomware recovery workflows and strategic risk narratives built at the CISO level.
Threat intelligence demand shifts from “IOC feeds” to operational intelligence services
By 2030, a threat-intel team that only produces reports will be considered overhead. Hiring managers will pay for intel professionals who deliver operational services: detection enrichment, prioritization, campaign mapping, and actionable guidance during active incidents. That requires tight integration with CTI collection and analysis, and an understanding of how threat signals flow into SOC workflows described in the SOC manager path.
Threat intelligence also expands into compliance and executive communication. Leadership wants answers like: “Are we being targeted?” “What’s most likely to hit our industry?” “What controls reduce that risk fastest?” Those questions must map to governance and frameworks, including regulatory pressure explained through cybersecurity compliance trends and structured risk reporting supported by a programmatic leadership approach like the director of cybersecurity roadmap.
The macro constraint that keeps demand high: workforce shortages
Even when budgets grow, staffing remains hard. That pushes specialization because fewer people must do higher-impact work. Threat intelligence and ethical hacking are “force multipliers” because they either prevent incidents or reduce wasted SOC time. This is reinforced by ACSMI’s research on the cybersecurity workforce shortage, and it shows up operationally when teams must automate enrichment and response via structured plans like an incident response framework.
3) What “Specialized” Means in 2026: Skills That Separate Top Candidates
Ethical hackers are expected to be business-aware, not just technically skilled
The highest-demand ethical hackers can explain impact in business terms and prioritize what matters. They understand where security breaks in real organizations: identity sprawl, insecure APIs, misconfigured cloud, and weak segmentation. They also communicate clearly and deliver fixes that map to security outcomes, not just findings.
A clean pathway into ethical hacking begins with the foundations in the CEH step-by-step guide, then expands into deeper specialization such as the endpoint and detection ecosystem discussed in endpoint security analysis and the network fundamentals that still matter in investigations, including firewall technologies and IDS deployment.
Ethical hackers who understand cryptography, key management, and secure protocols stand out because they can evaluate real data protection risk, not just exploit code. That knowledge is grounded in PKI components and modern encryption standards.
Threat intelligence roles split into distinct tracks
Hiring managers increasingly separate threat intelligence into roles with different outputs:
Collection and validation specialists who build reliable sources and pipelines aligned with CTI collection workflows.
Operational intel analysts who enrich alerts and feed detections into the SIEM.
Campaign analysts who track ransomware and phishing patterns and translate them into controls, supported by research like phishing prevention strategy and ransomware threat analysis.
Executive-facing intelligence communicators who connect threat posture to governance frameworks like NIST adoption and regulatory expectations described in GDPR and cybersecurity.
To stay competitive by 2030, CTI candidates must show they can convert intel into decisions. That includes understanding how attackers behave, how defenders detect, and how teams respond using a robust incident response plan.
Quick Poll: What’s Your Biggest Hiring Bottleneck for Specialized Cyber Roles?
Pick the issue that hurts most. This is usually why teams stay reactive even with “good tools.”
4) How Organizations Will Structure These Teams by 2030
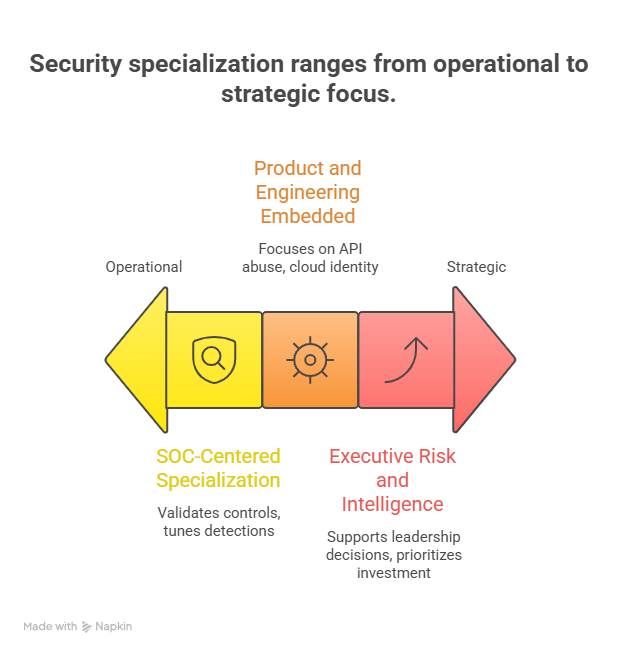
Model A: “SOC-centered specialization”
In this model, ethical hackers and threat intelligence sit close to the SOC and incident response function. Ethical hacking validates controls and generates realistic attack scenarios. Threat intelligence tunes detections and guides hunts. The SOC acts faster because it has better context and fewer dead-end alerts, which is the operational evolution described in SOC progression.
This model works best when your SIEM and detection stack is mature, aligned to SIEM best practices, and your team can execute consistent containment through an incident response plan.
Model B: “Product and engineering embedded specialization”
High-growth SaaS companies increasingly embed ethical hackers into product security and embed threat intelligence into detection engineering. Ethical hackers focus on API abuse, auth flows, and cloud identity misuse. Threat intelligence focuses on real campaign patterns and how those patterns should influence detection and rate-limiting strategies.
This model benefits from strong security engineering fundamentals around cryptography and trust, supported by PKI foundations and practical encryption standards, plus governance alignment under frameworks like NIST adoption.
Model C: “Executive risk and intelligence function”
Some organizations will build an intelligence function that directly supports leadership decisions: vendor risk, geographic threat shifts, regulatory pressure, and crisis response. This model grows as cybersecurity becomes a board-level risk, the same leadership pressure addressed in the CISO pathway and the director-level roadmap.
In this model, threat intelligence is not “nice to have.” It is the engine that prioritizes investment and justifies spend with measurable outcomes, using market context like ACSMI’s global cybersecurity market outlook and regional considerations such as cybersecurity in North America.
5) Career Pathways That Match 2026–2030 Demand
If you want to ride the demand wave, stop optimizing for titles and start optimizing for skill leverage. Ethical hacking and threat intelligence reward people who can produce outcomes under uncertainty.
Ethical hacking pathway (high leverage, high demand)
Start with a strong foundation in offensive fundamentals and professional reporting through the CEH guide. Then build specialization that hiring managers pay for: cloud identity misuse, API testing, and attack simulation mapped to detection improvement. Connect your offensive learning to defensive reality by understanding how teams respond during real incidents via IRP execution and how ransomware forces rapid decisions described in ransomware response.
As you mature, you become far more valuable if you can translate findings into executive-ready risk language, which is why long-term growth often points toward leadership tracks like the CISO roadmap.
Threat intelligence pathway (operational impact over vanity reports)
Start by mastering collection, analysis, and translation into action using CTI collection and analysis. Then learn how intelligence plugs into detection workflows through SIEM operations. Build the ability to influence playbooks and containment decisions through incident response.
To stand out, specialize in high-impact domains like phishing-driven initial access using phishing prevention analysis, ransomware campaigns via ransomware threat research, and endpoint telemetry interpretation supported by ACSMI’s endpoint security study.
Compensation and progression reality
Specialization pays when you can show measurable outcomes: fewer successful intrusions, faster containment, reduced false positives, and better prioritization. Long-term earning power often aligns with roles that connect technical truth to leadership decisions, especially for those moving from operational roles into the governance tracks described in the director roadmap and CISO path.
6) FAQs: Ethical Hacking and Threat Intelligence Demand (2026–2030)
-
Both will grow, but for different reasons. Ethical hacking grows because organizations need proof their controls work in real attack paths, especially with ransomware pressure described in ransomware response and recovery. Threat intelligence grows because teams cannot triage unlimited alerts and need prioritization and enrichment integrated into SIEM operations. In practice, the highest-demand teams pair both: hackers find real weaknesses, and intel helps the SOC focus on threats that are actually active.
-
Operational intel changes decisions. It enriches detections, guides hunts, triggers playbook updates, and influences containment steps that align with an incident response plan. It also supports detection engineering by mapping threats to telemetry pipelines in a SIEM. If intel does not reduce response time or prevent incidents, it is not operational.
-
Focus on real-world intrusion paths: identity abuse, cloud misconfigurations, API vulnerabilities, and endpoint-to-cloud pivots. Build credibility through structured learning and reporting via the CEH guide, then align your work with how defenders actually operate using IRP execution. Staying relevant also means understanding modern data protection fundamentals such as PKI and encryption standards.
-
It filters noise by identifying which alerts match active campaigns, meaningful TTPs, and relevant targeting patterns. That makes detection tuning sharper inside the SIEM, and it improves response choices under stress via a consistent incident response plan. When threat intelligence is integrated properly, analysts spend less time chasing dead ends and more time containing real threats.
-
For many people, yes, because SOC work teaches what “actually happens” during incidents, how telemetry behaves, and how organizations make decisions under pressure. That experience is structured well through the SOC analyst to SOC manager pathway. But a direct ethical hacking start is also strong if you build professional discipline through the CEH step-by-step guide and connect your work back to response playbooks like IRP execution.
-
Industries with high downtime costs, high regulatory pressure, or high-value data tend to pay more and hire deeper specialization. They also invest more in compliance alignment and frameworks, which is why understanding topics like cybersecurity compliance trends and NIST adoption improves your long-term ceiling. In any industry, demand spikes when ransomware risk is existential, which is why knowledge anchored in ransomware response stays valuable.
-
For ethical hacking, build structured fundamentals and credible deliverables using the CEH roadmap, then specialize in practical testing areas like web apps, cloud identity, and API abuse. For threat intelligence, master collection and analysis through CTI workflows, then learn to operationalize intel inside SIEM processes and response operations guided by an incident response plan. In both tracks, the shortcut is not “more tools.” The shortcut is proving you can produce outcomes.